How serious is the cyber threat?
According to the World Economic Forum, cyber attacks rank third out of the 10 most likely risks threatening humanity, ahead of large scale migration (sixth) and terrorist attacks (eigth). Indeed, the probability of experiencing a cyber attack is currently one in four.
What are the greatest cyber risks?
There are a wide range of risks including: client data breaches, internal hacking, ransomware, phishing attacks, computer viruses, cryptocurrency hijacking and DDoS — distributed denial of service attacks via botnets. 48% of cyber attacks are criminal or malicious attacks. The top assets targeted are databases (servers) at 20% and POS terminals (user devices) at roughly 18%. Personal data, at 40%, and payment data, at 35%, are most often compromised. The average cost of resolving one record hacked is US$157.
How much is being spent on cyber security?
Cyber security is growing fast and expenditure is expected to grow to US$170 billion by 2020 from US$3.5 billion in 2004. While it has been jumping to catch up with cyber crime, it has not succeeded in curbing cyber damages which are currently estimated at topping US$2.1 trillion in 2018 and reaching US$2.5 trillion by the end of 2020. Asean countries alone suffered losses of US$750 billion.
What is the available coverage for cyber insurance?
Insurance companies seem to be lagging behind in valuing cyber risks and thus providing differentiated coverage. The maximum cyber coverage available for each firm is only US$300 million. A breach involving 50 million records costs an average of US$350 million.
The value of the overall insurance market is expected to grow to US$4.6 billion in premiums by 2023. The relatively small volume in relation to the size of the risk is in part due to insurance companies not yet coming to grips with how to value cyber risks in dollars and cents. The cyber field and finance are not truly in sync yet. C-level executives in companies are hard pressed to squeeze financial data about risk and return out of their technically oriented IT teams.
What are the advantages of valuing cyber risk?
Putting detailed financial risk numbers to cyber risk will help grow the cyber liability risk business for insurers and reinsurers. Although cyber liability insurance is developing, it is well behind where it should be, partly because insurers cannot accurately quantify cyber risks. In addition, the shear dimensions of cyber damages are overwhelming — these damages are often hard to quantify in final terms. For example, what is the impact of a cyber attack on the equity value of a company? The only costs currently being considered are immediate expenses.
Financially quantifying cyber risks allows insurers to adjust premiums, select insurable cyber risks rather than others, and thus drive their cyber insurance business.
What can be done to help insurers come to grips with cyber risks?
Insurers wear two hats in the cyber world. First, by offering cyber liability coverage, and second, by themselves being major targets of cyber attacks. Insurers harbour the data of billions of people on a worldwide scale. They hold the type of data which is most likely to invite cyber attacks.
Thus, insurers are fighting cyber crime on both fronts. It is therefore important they use methods which enable them to quantify the total and changing risk exposure of themselves and their clients to cyber threats. They should ask: what is my total risk exposure right now? What is my risk in terms of costs (for example lost productivity, litigation and regulatory fines) and in terms of the value of my company? And which is the best way to capture all these risks in a single metric, such as a discount rate?
How accurately can you assess the value at risk and how?
Financial executives use discount rates to quantify the general risk exposure of their companies. These rates are used to discount future cash flows to a net present value and functions as a metric to value a unit or company. With cyber growing to a major threat to the operations and value of a company, it should be added a component of the corporate discount rate.
Value at Cyber Risk (VaCR) is developed by Management & Excellence and offered in Hong Kong with Moore Stephens; it quantifies all cyber risks at any one time in terms of a cyber discount rate. With VaCR, all cash flows and the company’s value can be discounted using this rate. Even more importantly, VaCR calculates cyber risks as they fluctuate. If, for example, a company institutes a new measure to combat cyber breaches, VaCR can adjust the risk level in the company accordingly.
Insurers benefit doubly from VaCR: they can better structure cyber liability insurance and can assess/improve their own cyber risk exposure.
What is a cyber threat assessment?
This involves undertaking a complete technical, strategic and financial review of the areas of a company which determine its cyber risk level; from IT systems to its governance and HR policies. Roughly one-third of cyber breaches can be traced to current and former employees and suppliers. Negligence is a major source of cyber risk. A good cyber threat assessment will also involve tapping into world data flows and measuring the sources and levels of specific threats to a company. Only highly developed cyber specialists have access to these data flows.
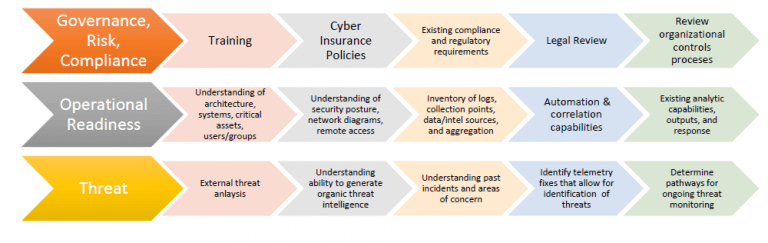
What does a cyber threat turnaround strategy involve?
This involves a range of tasks including: integrating enhancements into the collection, aggregation and correlation capabilities to increase data accuracy, consistency, visibility or analytic capabilities.
In addition: upgrading or altering cyber insurance policies to account for increased risk; automating manual processes that support data collection or analytics to improve the timeliness, normalisation and consistency of data processing.
Other methods involve: generating improved incident response playbooks; identifying new training methods or sources; tightening the integration of data sources into the data processing pipeline to improve context, priority, and filtering.
Noise reduction and data labeling should be used where possible, for example scanning devices, back-up activity, and trusted external or cloud connections; there are quick wins filling gaps within the current capability, for example rules, signatures and dashboards to improve collection, visibility or capability to aid the company’s threat intelligence and hunt teams.
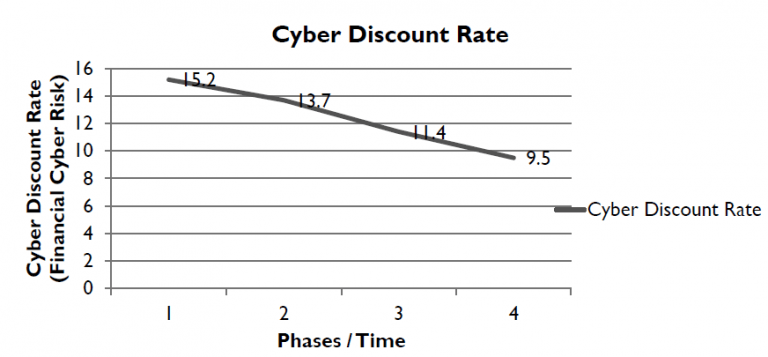
Can you monitor cyber threats in real time?
Yes. In essence this involves translating technical and organisational data into financial data which are expressed in a VaCR cyber discount rate. This rate should be declining as the turnaround strategy takes effect:
This article was written by William Cox , chief executive of Management & Excellence, which is based in Madrid and New York.
-
Cybersecurity: The false promise of flawed certifications
- April 23
There is little correlation between certifications and avoiding breaches as the cybersecurity landscape evolves too quickly for annual checkups to be sufficient.
-
Trade credit: Amid trade war, APAC firms must stay agile and ensure adequate protection
- April 2
The US has implemented a new tariff regime across industries and countries, with import duties being a central aspect of US economic and foreign policy. These measures aim to protect domestic industries from what the US government perceives as unfair trade practices, global excess capacity, and imbalanced trading relationships. The policy includes mainland China, delayed […]
-
Insurtech: Tech predictions for the insurance sector in 2025
- January 27
2024 was the year we saw signs that the insurance industry is rapidly transitioning from experimenting with generative AI (GenAI) to deploying scaled production use cases. Fuelled by new data streams and advancements in IOT, and wearables, predictive capabilities are reaching new heights. However, prediction alone is insufficient to reduce loss ratios systemically; meaningful impact […]
-
2004 tsunami: Loss, and lessons: reckoning with the Indian Ocean tsunami 20 years on
- December 20
Though two decades have passed, the 2004 Indian Ocean tsunami is still fresh in my memory. I was in Australia at the time. It was a warm summer’s day, with many people starting to watch the Boxing Day test cricket match between Australia and Pakistan in Melbourne, when the news first hit. Like all of […]
-
Allianz General | Allianz General combines innovative protection solutions while powering social good to lead Malaysian market
The insurer proactively addresses emerging risks and evolving customer protection needs while giving back to the community.
-
Sedgwick | Asia’s Energy Transformation – Balancing Growth, Risk and Renewables
Energy market presents unique risks, especially in a region which includes China and Japan as well as developing nations like Vietnam and the Philippines.
-
Beazley | Turbulent Waters: the maritime energy transition challenge
Businesses are facing a complex transition to non-carbon energy sources amid a push to achieve net-zero emissions for the marine sector by 2050.
-
Aon | Navigating shifts in the global and Asia insurance markets
Neelay Patel, Aon head of growth for Asia, says the market in Asia is at an ‘interesting stage of the cycle’.


William Cox, Management & Excellence
Evaluating the cyber risk threat
William Cox, Management & Excellence